🛡️ What Is a Firewall?
A firewall is a critical component of network security that acts as a barrier between trusted internal networks and untrusted external connections, such as the internet. It monitors, filters, and controls incoming and outgoing network traffic based on predefined security rules, helping prevent unauthorized access, data breaches, and cyberattacks.
In simple terms, a firewall works like a security checkpoint—it inspects every packet of data entering or leaving the network, allowing or blocking it according to configured policies.
🛡️ Why Firewalls Matter in Modern Networks
With today’s increasing number of connected devices, network threats have become more sophisticated. Firewalls are the first line of defense in a layered security strategy, ensuring that only legitimate traffic passes through your systems.
Enterprises, data centers, and even home networks rely on firewalls to:
Block malicious or suspicious traffic
Prevent data leaks and intrusion attempts
Protect network-connected devices and servers
Enforce company-wide access control policies
By deploying a properly configured firewall, organizations can significantly reduce exposure to attacks such as ransomware, DDoS, or phishing.
🛡️ Main Types of Firewalls
Firewalls come in several types, each providing a different level of security and functionality. Understanding these categories helps network engineers and IT managers choose the right solution for their environment.
1. Packet-Filtering Firewall
The earliest and simplest type of firewall examines network packets based on IP address, port, and protocol. Although lightweight, it lacks advanced context awareness.
2. Stateful Inspection Firewall
Also known as a dynamic packet-filtering firewall, it tracks the state of active connections and allows packets that match a known active session. It offers improved security and is widely used in enterprise environments.
3. Proxy Firewall (Application-Level Gateway)
Acts as an intermediary between users and the internet, analyzing traffic at the application layer. This type provides deep inspection and hides the internal network’s structure, but may add latency.
4. Next-Generation Firewall (NGFW)
Modern NGFWs combine traditional filtering with intrusion prevention, deep packet inspection, and application awareness. They can detect sophisticated threats that older firewalls might miss.
🛡️ How a Firewall Works
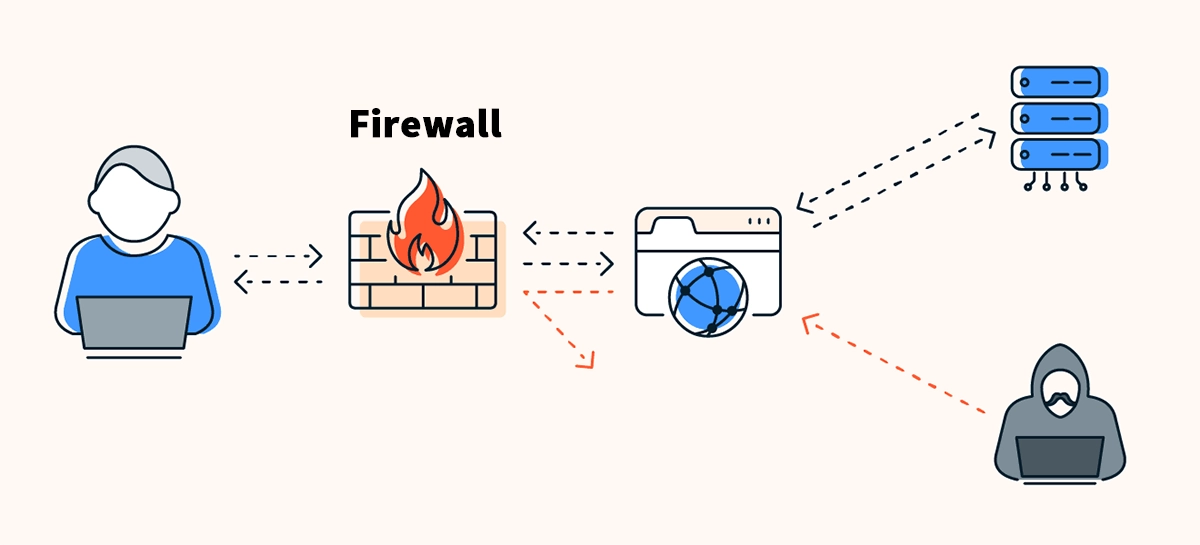
Incoming traffic reaches the firewall interface.
The firewall classifies packets by IP address, port, protocol, application, or user.
It compares the packets against predefined rules (allow, deny, inspect, proxy).
For stateful devices, only packets matching valid sessions are accepted.
Deep inspection or threat intelligence engines analyze suspicious flows before making a final decision.
🛡️ Firewall Best Practices for Stronger Network Security
To maintain robust protection, firewalls must be correctly configured and regularly maintained.
Here are key best practices followed by professionals:
Define Clear Security Policies: Establish which traffic is allowed or denied based on roles, applications, and network zones.
Regular Rule Review: Audit and update rules to remove outdated or redundant entries.
Enable Logging & Monitoring: Track firewall logs to detect unusual patterns or unauthorized access attempts.
Keep Firmware Updated: Regular updates ensure protection against new vulnerabilities.
Combine with Other Security Layers: Use firewalls alongside intrusion detection systems (IDS), VPNs, and endpoint security.
🛡️ Firewall Selection Checklist
Define the use case: perimeter, segmentation, or cloud protection.
Evaluate throughput and latency under full inspection load.
Check integration options with SIEM, IAM, and cloud APIs.
Ensure policy management is intuitive and auditable.
Review the total cost of ownership (TCO), including subscriptions and updates.
Confirm vendor transparency and frequency of security patches.
🛡️ How LINK-PP Supports Secure Network Infrastructure
At LINK-PP, we understand that secure connectivity starts at the hardware layer. Our range of magnetic RJ45 connectors, Ethernet transformers, and network interface modules are designed to ensure stable, EMI-resistant data transmission—essential for reliable communication between firewalls, switches, and routers.
Whether you’re designing an enterprise network or integrating PoE-enabled systems, LINK-PP components provide high-performance, signal integrity, and long-term reliability—helping your firewall solutions operate with maximum efficiency.
Explore LINK-PP’s RJ45 connectors and magnetics to build secure and high-speed Ethernet systems that meet modern cybersecurity demands.
🛡️ FAQs
What’s the difference between a firewall and an IPS?
A firewall enforces access rules and filters traffic, while an Intrusion Prevention System (IPS) analyzes packets for malicious content and blocks attacks. Most Next-Generation Firewalls combine both functions.
Are software firewalls as effective as hardware firewalls?
It depends on the use case. Host-based software firewalls are essential for endpoint security, while hardware or virtual firewalls handle large-scale perimeter protection. The best approach combines both.
How often should firewall rules be reviewed?
Firewall policies should be reviewed at least quarterly or whenever major network changes occur to maintain security compliance and performance.
🛡️ Conclusion
Firewalls remain a cornerstone of network security, protecting data, systems, and users from a growing range of cyber threats.
By understanding their types, functions, and configuration best practices—and pairing them with trusted components from LINK-PP—you can create a more secure, resilient, and high-performance network infrastructure.