Have you ever wondered what happens behind the scenes when you run a ping command or get a "Destination Unreachable" error? The answer lies in a fundamental, yet often overlooked, protocol that keeps the internet running smoothly: the Internet Control Message Protocol (ICMP).
While protocols like TCP and TCP get all the glory for delivering your data, ICMP works tirelessly in the background as the internet's diagnostic and control messenger. In this comprehensive guide, we'll unpack what ICMP is, how it works, and why it's indispensable for network health. We'll also explore how the physical hardware, like high-performance optical transceivers, plays a crucial role in ensuring these messages are delivered reliably.
⚙️ Key Takeaways
ICMP helps you spot network problems. It sends messages about errors and connection issues.
You can use tools like ping and traceroute to test your network. These tools use ICMP to check if devices are online. They also show the path your data takes.
ICMP sends important error messages. For example, it can say 'Destination Unreachable' if data cannot reach its target.
Watch out for security risks with ICMP. Attackers can use it for attacks like DDoS. You should limit extra ICMP traffic to keep your network safe.
ICMP is not for sending normal data. Use it for network management and fixing problems instead.
⚙️ What is ICMP?
ICMP is a network-layer protocol used by network devices—like routers, switches, and servers—to communicate operational information and error messages. It's not designed to carry application data but to report on the status of the network itself.
Think of it this way: If data packets are the letters and packages sent through the postal service, ICMP is the system of delivery notifications, "return to sender" slips, and "address not found" memos that keep the postal system efficient.
A key thing to remember: ICMP is a supporting protocol, primarily used by network administrators and advanced network troubleshooting tools to diagnose connectivity issues.
⚙️ How Does ICMP Work? The Core Mechanism
ICMP operates by sending special messages known as ICMP packets or datagrams. These messages are encapsulated within IP packets but are considered part of the Internet Protocol suite (TCP/IP). Since ICMP messages are carried in IP packets, they are connectionless, meaning no established connection is required to send an ICMP message.
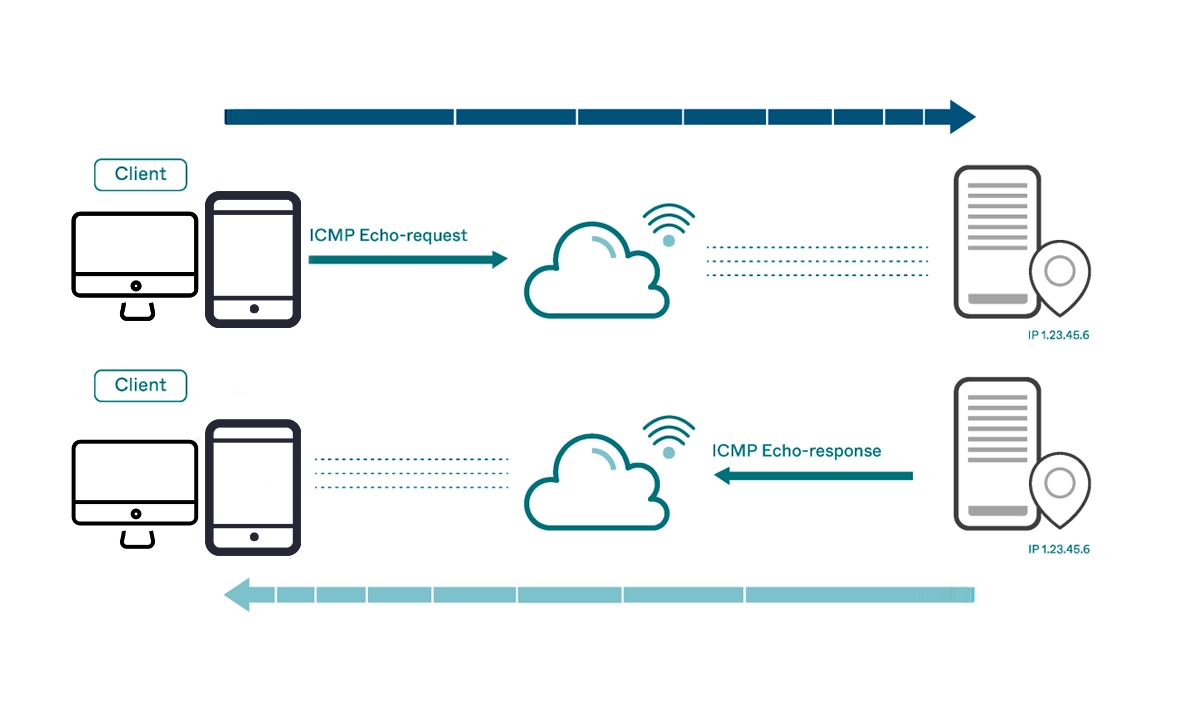
The most common ICMP message types involve a request and a reply. For example, when you ping a website, your computer sends an ICMP Echo Request. If the host is available and able to respond, it sends back an ICMP Echo Reply. This simple exchange confirms reachability and measures round-trip time.
⚙️ Common ICMP Message Types and Their Roles
ICMP has a variety of message types, each with a specific code to provide detailed information. Here is a table summarizing the most critical ones:
ICMP Type | Name | Common Use Case |
|---|---|---|
0 | Echo Reply | Response to a Ping request (Echo Request). |
8 | Echo Request | Used by the ping command to check host reachability. |
3 | Destination Unreachable | Indicates a packet could not be delivered. Contains codes for specific reasons (e.g., network/host/protocol unreachable). |
11 | Time Exceeded | Sent when a packet's TTL (Time to Live) reaches zero. Crucial for the traceroute command. |
5 | Redirect | Instructs a host to use a better gateway for a specific destination. |
4 | Source Quench | (Largely obsolete) Used to request a sender to slow its transmission rate. |
These messages form the backbone of essential network diagnostics. For instance, when optimizing a network path for low-latency applications, engineers rely on tools like traceroute (which uses Type 11 messages) to identify bottlenecks, ensuring their infrastructure—including critical components from vendors like LINK-PP—is performing optimally.
⚙️ ICMP in Action: Ping and Traceroute
Let's break down two of the most common utilities that rely on ICMP:
Ping: This is the simplest network diagnostic tool. It uses ICMP Echo Request (Type 8) and Echo Reply (Type 0) messages to test whether a remote host is alive and to measure the latency (response time) between two points. A successful ping is the first sign of a healthy connection.
Traceroute (or Tracert on Windows): This clever utility maps the path packets take to reach a destination. It sends packets with progressively increasing TTL values. Each router along the path decrements the TTL and, when it hits zero, sends an ICMP Time Exceeded (Type 11) message back to the source. By collecting these messages from each hop, traceroute builds a visual map of the route.
Understanding how to use these tools is a fundamental skill for anyone managing network infrastructure and seeking effective solutions for network latency issues.
⚙️ The Dark Side: ICMP and Security
While incredibly useful, ICMP can be exploited for malicious purposes. Common attacks include:
ICMP Flood (Ping Flood): A type of Denial-of-Service (DoS) attack where the attacker overwhelms a target with a flood of ICMP Echo Request packets.
Smurf Attack: An amplification attack where an attacker spoofs the source IP address and sends broadcast pings, causing all hosts on the network to reply to the victim, flooding it with traffic.
Due to these risks, many corporate firewalls are configured to block certain types of ICMP traffic. However, blocking all ICMP can "break" helpful network functions and make legitimate network performance monitoring more difficult. A balanced security approach is key.
💡 Pro Tip: Instead of blocking all ICMP, consider rate-limiting ICMP traffic on your network perimeter to mitigate flood attacks while preserving diagnostic capabilities.
⚙️ The Unsung Hero: How Optical Transceivers Enable Reliable ICMP
You might be wondering: what does physical hardware have to do with a network protocol? The answer is: everything. ICMP messages, like all network traffic, travel as pulses of light through fiber optic cables. The devices that convert electrical signals (from network equipment) into light signals (for the fiber) and back are called optical transceivers.
The performance and reliability of these transceivers directly impact the integrity of all network communications, including ICMP. A faulty or low-quality transceiver can introduce errors, packet loss, and increased latency, which would directly skew your ping and traceroute results.
For a robust network infrastructure, using high-quality, compatible transceivers is non-negotiable. For instance, the LINK-PP 100G QSFP28 LR4 optical module is an excellent choice for high-speed data center interconnects, offering a transmission distance of up to 10km with exceptional signal integrity. By ensuring your physical layer is built with reliable components like LINK-PP transceivers, you guarantee that your diagnostic protocols like ICMP can function accurately, providing a true picture of your network's health.
⚙️ Conclusion: ICMP is Indispensable
ICMP is the silent, ever-present guardian of network communication. From a simple connectivity check to complex path discovery, it provides the critical feedback necessary to maintain and troubleshoot modern networks. While security considerations are important, its value in enabling robust network management and diagnostics cannot be overstated.
By understanding ICMP and pairing it with a high-performance physical network foundation—including reliable optical transceivers—you can build, manage, and optimize a faster, more resilient, and more efficient network.
⚙️ FAQ
What is the main purpose of ICMP?
ICMP helps you find and report network problems. You use it to get error messages and test if devices can talk to each other.
What types of messages does ICMP send?
ICMP sends error messages and information messages. You see messages like "Destination Unreachable," "Time Exceeded," and "Echo Reply" when you use network tools.
What tools use ICMP for network testing?
You use tools like ping and traceroute. Ping checks if a device is online. Traceroute shows the path your data takes across the network.
What risks come with allowing ICMP traffic?
Attackers can use ICMP for attacks like DDoS or to hide data. You lower your risk by blocking unneeded ICMP types and watching for strange traffic.