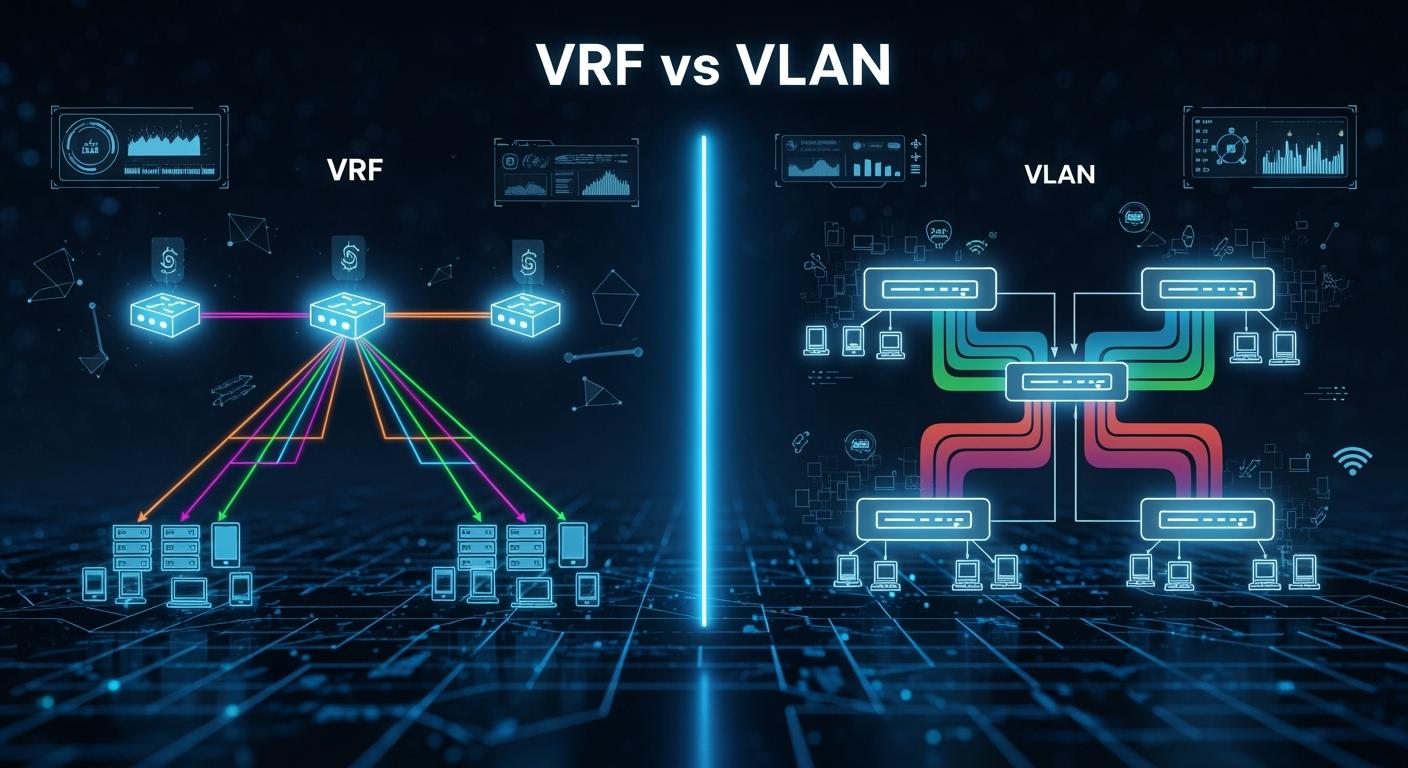
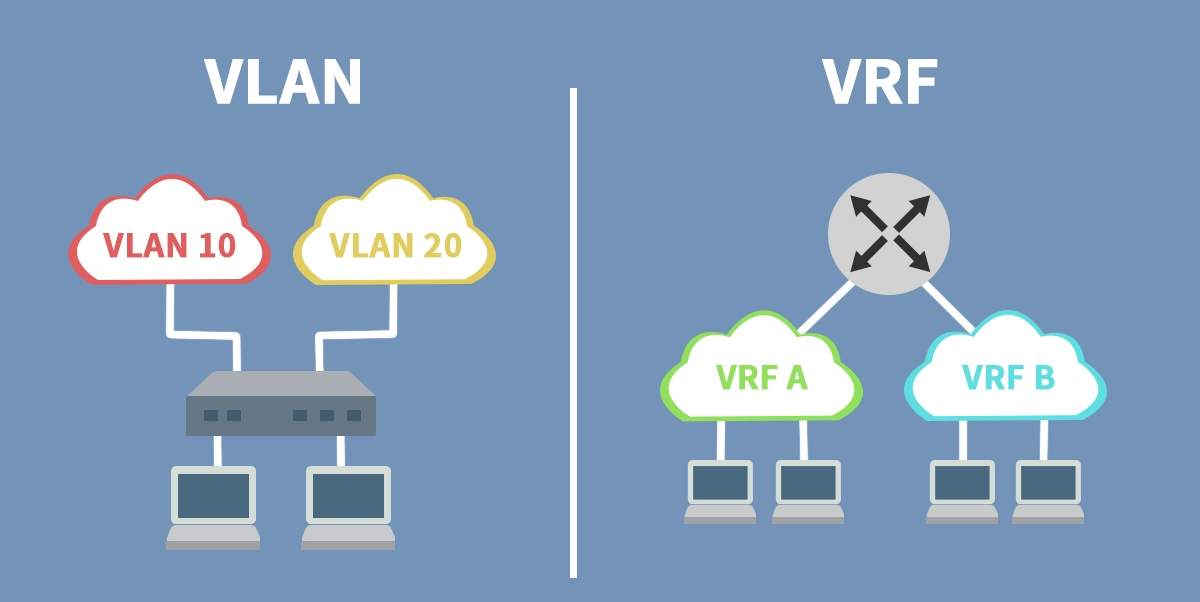
In the complex world of network architecture, creating logical, isolated networks is a fundamental requirement for security, management, and performance. Two dominant technologies have emerged to meet this need: the veteran VLAN and the more robust VRF. While they might seem similar on the surface, understanding their core differences is crucial for designing scalable and secure modern networks.
This guide will break down VRF and VLAN, compare them head-to-head, and help you decide which technology—or combination—is right for your enterprise network segmentation strategy.
📄 Key Takeaways
VRF works at Layer 3. It lets one device have different routing tables for each network. This helps keep networks safe and manage traffic better.
VLAN works at Layer 2. It puts devices into groups by switch ports. This helps control traffic and keeps the network organized.
Use VRF when you need strong separation between networks. This is good for service providers or big companies. It helps keep important data safe.
Pick VLAN for easier setups. It is good for splitting guest and staff devices in offices or schools. This keeps their traffic apart without trouble.
Using both VRF and VLAN together gives more security and flexibility. You get strong separation and can group devices well.
📄 What is a VLAN? (Virtual Local Area Network)
A VLAN (Virtual Local Area Network) is a technology that allows you to create multiple, distinct broadcast domains on a single physical network switch. Think of it as creating virtual, independent switches within a single physical device. It operates at Layer 2 (the Data Link layer) of the OSI model.
Key Characteristics of VLANs:
Layer 2 Segmentation: Isolates broadcast traffic, improving network performance and security.
VLAN ID: Each VLAN is identified by a unique ID (1-4094), tagged in the Ethernet frame header (IEEE 802.1Q).
Simplicity & Ubiquity: A widely supported, fundamental feature on nearly every managed switch.
Common Use Cases: Separating departments (e.g., Finance, HR, Engineering), creating guest networks, and isolating IoT devices.
Essentially, VLANs are the bedrock of network segmentation, preventing a broadcast storm in the marketing department from taking down your entire core financial operations.
📄 What is VRF? (Virtual Routing and Forwarding)
VRF (Virtual Routing and Forwarding) takes segmentation to the next level by creating virtualized routing tables within a single physical router or Layer 3 switch. It operates at Layer 3 (the Network layer). Each VRF instance maintains its own separate routing table, interfaces, and forwarding information.
Key Characteristics of VRFs:
Layer 3 Segmentation: Isolates IP routing domains. Overlapping IP addresses (e.g., 192.168.1.0/24) can exist in different VRFs without conflict.
Independent Routing Tables: Each VRF has its own instance of routing protocols (OSPF, BGP) and static routes.
Enhanced Security: Provides true multi-tenant isolation at the IP level, crucial for service providers and large enterprises.
Common Use Cases: Multi-tenancy environments, network segmentation for security zones (e.g., PCI-DSS compliance), and creating separate paths for production and development networks.
In short, while a VLAN creates a virtual switch, a VRF creates a virtual router inside your physical device.
📄 VRF vs VLAN: The Head-to-Head Comparison
The following table provides a clear, side-by-side comparison of these two pivotal technologies for anyone planning a secure and scalable data center network design.
Feature | ||
|---|---|---|
OSI Layer | Layer 2 (Data Link) | Layer 3 (Network) |
Primary Function | Broadcast Domain Segmentation | Routing Table Isolation |
Overlapping IPs | Not Possible | Yes, Possible |
Scope | Typically limited to a single LAN or switched network | Can extend across an entire routed network (WAN/L3 domain) |
Complexity | Lower, easier to configure and manage | Higher, requires advanced routing knowledge |
Security | Good (L2 isolation) | Excellent (L3 isolation, prevents route leakage) |
Common Use Case | Departmental segmentation, Guest Wi-Fi | Multi-tenancy, MPLS VPNs, strict security zones |
📄 The Physical Backbone: The Role of Optical Transceivers
No discussion about logical network design is complete without acknowledging the physical layer that makes it all possible. High-speed interconnects between switches, routers, and servers are the lifelines that carry your VLAN-tagged and VRF-routed traffic.
This is where high-quality optical transceivers become critical. They convert electrical signals from network devices into light pulses for transmission over fiber optic cables. For a robust network infrastructure, especially one handling multiple VRFs or high-throughput VLANs, reliability and compatibility are non-negotiable.
Choosing the right transceiver ensures low latency, high bandwidth, and stable links, preventing physical layer issues from undermining your sophisticated logical segmentation. For instance, using a trusted brand like LINK-PP for your core and distribution switches guarantees performance and reduces compatibility headaches. A specific model like the LINK-PP SFP-10G-SR is a workhorse for 10GbE connections over multimode fiber within data centers, forming the reliable bridge between your segmented devices.
📄 How to Choose: VRF, VLAN, or Both?
The choice isn't always mutually exclusive. In fact, they are often used together in a complementary fashion.
Use VLANs when:
You need simple, Layer 2 segmentation within a building or campus.
Your goal is to reduce broadcast traffic and improve LAN performance.
You are segmenting devices that don't require complex routing policies between them.
Budget and technical expertise are primary concerns.
Use VRF when:
You require complete isolation of IP routing domains, especially with overlapping IP address spaces.
You are a service provider offering MPLS VPN services to multiple customers.
You need to enforce strict security policies between different business units (e.g., separating corporate from production networks).
Your network segmentation strategy spans a large, routed infrastructure.
Use them together in a classic design:
Use VLANs for access-layer segmentation (e.g., one VLAN per user group).
Use VRF at the core/distribution layer to route traffic between these VLANs in isolated routing instances.
This layered approach is a cornerstone of modern cybersecurity and network management, providing defense-in-depth.
📄 Final Thoughts and Next Steps
Both VRF and VLAN are powerful tools in a network architect's toolkit. VLANs offer a straightforward, effective method for basic segmentation, while VRFs provide a robust, carrier-grade solution for complex, multi-tenant environments requiring strict Layer 3 isolation. Understanding their distinct roles is the first step toward building a more resilient and secure network.
📄 FAQ
What is the main difference between VRF and VLAN?
You use VRF to separate routing tables at Layer 3. VLAN splits devices into groups at Layer 2. VRF controls network paths. VLAN controls device traffic on switches.
Can you use VRF and VLAN together?
Yes, you can combine VRF and VLAN. You group devices with VLAN, then use VRF to keep routing paths separate. This gives you stronger isolation and better security.
Which is easier to set up, VRF or VLAN?
You find VLAN easier to set up. You assign switch ports to groups. VRF needs more planning and configuration. You manage routing tables and network paths.
When should you choose VRF over VLAN?
You choose VRF when you need strong isolation between networks or departments. VRF works best for service providers or large companies. VLAN fits small networks or simple device grouping.
Do VRF and VLAN improve network security?
Both improve security. VLAN keeps device traffic apart on switches. VRF separates routing paths and network traffic. You get stronger protection when you use both together.