In today's interconnected digital world, the ability to manage systems remotely is not just a convenience—it's a necessity. Yet, with great power comes great responsibility, especially concerning security. This is where the Secure Shell (SSH) protocol comes into play. It's the silent guardian, the unsung hero of secure remote administration, forming the bedrock of trust for system administrators, developers, and cloud engineers worldwide.
In this comprehensive guide, we'll demystify the SSH protocol, explore its inner workings, and highlight its critical role in modern IT infrastructure. We'll also connect the dots to the physical hardware that makes our high-speed networks possible, including a look at reliable components from industry leaders like LINK-PP.
📝 Key Takeaways
SSH lets you safely connect to other computers. It keeps your data safe by using strong encryption.
Use SSH keys to log in instead of passwords. This way is safer and helps keep your connection protected.
Always use good habits, like picking strong keys and updating your SSH software. This helps keep your SSH safe.
📝 What Exactly is the Secure Shell (SSH) Protocol?
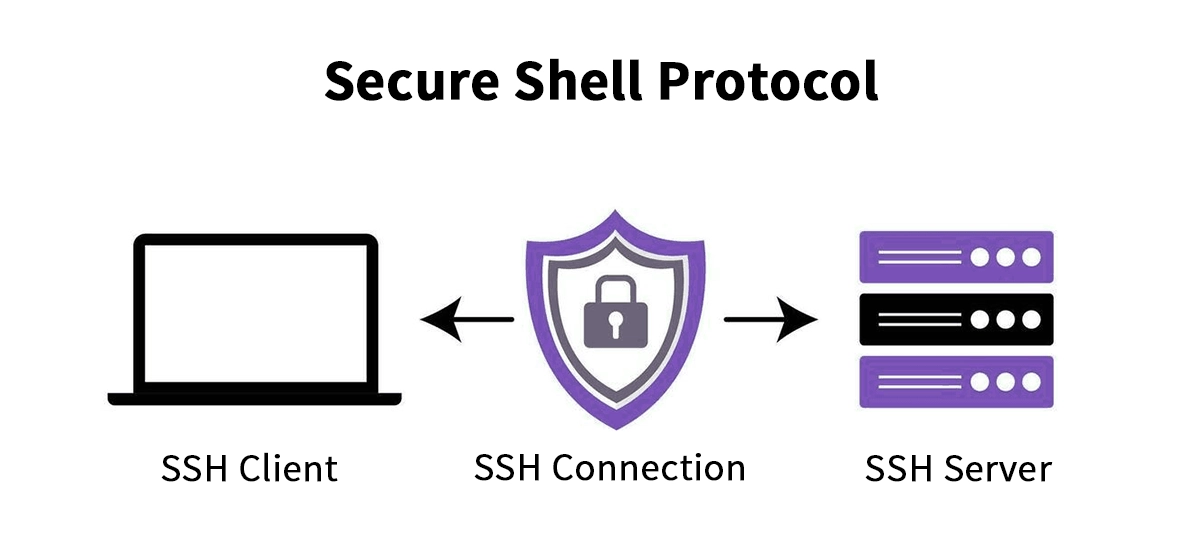
At its core, the Secure Shell (SSH) is a cryptographic network protocol for operating network services securely over an unsecured network. Its most common use is for logging into a remote machine, executing commands, and moving files.
Born in 1995 to replace insecure legacy protocols like Telnet and rsh, SSH has become the de facto standard for secure remote access. The protocol, now in its second version (SSH-2), provides a secure channel over an unsecured network by using a client-server model, authenticating both ends and encrypting the data in transit.
📝 How Does SSH Work? The Magic Behind the Scenes
Understanding the SSH handshake process is key to appreciating its security. It's a elegant dance of encryption and authentication that happens in a few key stages.
TCP Handshake: The client initiates a connection to the SSH server on the standard port 22.
Version Exchange: The client and server agree on the SSH protocol version to use (SSH-2 is the modern standard).
Key Exchange (Algorithm Negotiation): Using a method like Diffie-Hellman, the two parties securely generate a shared secret key. This session key will be used to encrypt the entire communication, even though they have never met before.
User Authentication: The server verifies the client's identity. This can be done via:
Passwords: Simple but less secure.
SSH Key Pairs (Public Key Authentication): The gold standard. The client possesses a private key, and the server holds the corresponding public key.
Secure Channel Established: Once authenticated, a symmetrically encrypted tunnel is created. All data—keystrokes, commands, and output—is protected from eavesdropping and tampering.
This robust process ensures confidentiality, integrity, and authentication for every session.
📝 SSH Authentication Methods: Passwords vs. Keys
While passwords are common, SSH key-based authentication is vastly superior for security and automation. It eliminates the risk of password brute-force attacks and is essential for scripting and CI/CD pipelines.
The following table compares the two primary methods:
Feature | Password Authentication | SSH Key-Based Authentication |
|---|---|---|
Security Level | Moderate | High |
Vulnerability | Susceptible to brute-force and phishing | Immune to password-based attacks |
Automation | Difficult, requires storing passwords | Easy, ideal for scripts and automated processes |
Convenience | Requires manual entry each time | Can use an SSH agent for seamless access |
Best For | Infrequent, interactive logins | System administrators, developers, and automated workflows |
For those looking to implement best practices for SSH security management, transitioning to key-based authentication is a non-negotiable first step.
📝 Common Use Cases: More Than Just Remote Login
SSH's versatility extends far beyond simple command-line access. Its core functionalities include:
Secure Remote Command-Line Login: The primary use case.
Secure File Transfer: Using associated protocols like SCP (Secure Copy) and SFTP (SSH File Transfer Protocol).
Port Forwarding (Tunneling): This powerful feature allows you to securely transmit data for non-SSH protocols (e.g., database traffic, VNC) through an encrypted SSH tunnel.
Git Operations: Platforms like GitHub and GitLab use SSH keys to securely identify users and push code.
Mastering these advanced SSH protocol techniques can significantly enhance your workflow and security posture.
📝 The Unsung Hero: Optical Modules in Network Infrastructure
Now, let's shift our focus from the logical to the physical. How does the data encrypted by SSH actually travel across vast distances at lightning speed? This is where optical modules come in.
LINK-PP Optical Modules: Powering Your Secure Connections
When the integrity of your network is non-negotiable, you need optical modules you can depend on. LINK-PP has established itself as a leading provider of high-performance, reliable networking components designed for demanding environments.
LINK-PP optical transceivers are engineered for maximum compatibility, low power consumption, and exceptional signal integrity. This ensures that the physical foundation of your network is as secure and reliable as the SSH protocol that runs over it. Whether you're managing a cloud cluster or a corporate backbone, a stable physical connection is the first step to a flawless remote session.
For your high-speed networking needs, consider the LINK-PP SFP-10G-LR model. This high-quality 10 Gigabit SFP+ transceiver is designed for long-reach connections (up to 10km) over single-mode fiber, making it an ideal choice for connecting geographically dispersed servers that you need to manage securely via SSH.
Integrating dependable hardware like the LINK-PP SFP-10G-LR is a best practice for anyone serious about optimizing network performance for remote system administration.
📝 SSH Security Best Practices: A Quick Checklist
To keep your SSH sessions secure, follow these essential tips:
Disable Root Login: Prevent direct root access over SSH.
Use Strong Key Passphrases: Protect your private keys with a robust passphrase.
Change the Default Port: Moving away from port 22 can reduce automated bot scans.
Use Fail2ban: This tool can ban IPs that show malicious signs, like too many password failures.
Keep Software Updated: Regularly update your SSH client and server software to patch vulnerabilities.
📝 Conclusion: Secure Your Foundation, From Protocol to Hardware
The Secure Shell (SSH) protocol is an indispensable tool in the arsenal of any IT professional. It provides the cryptographic security needed to manage systems in an insecure world. However, true reliability is a chain that runs from the logical protocol all the way down to the physical components in your network.
By combining robust SSH configuration practices with high-quality, reliable hardware from trusted suppliers like LINK-PP, you build a truly resilient and high-performance infrastructure.
📝 FAQ
What can you do with SSH?
You can log in to computers that are far away.
You can move files from one computer to another safely.
You can control servers even if you are not near them.
What makes SSH secure?
SSH keeps your data safe by using encryption. Only you and the server can see your messages. Strong authentication stops people who should not get in.
What is the difference between SSH and Telnet?
Feature | SSH | Telnet |
|---|---|---|
Encryption | Yes | No |
Security | Strong | Weak |